SDE无法连接问题处理过程
分享
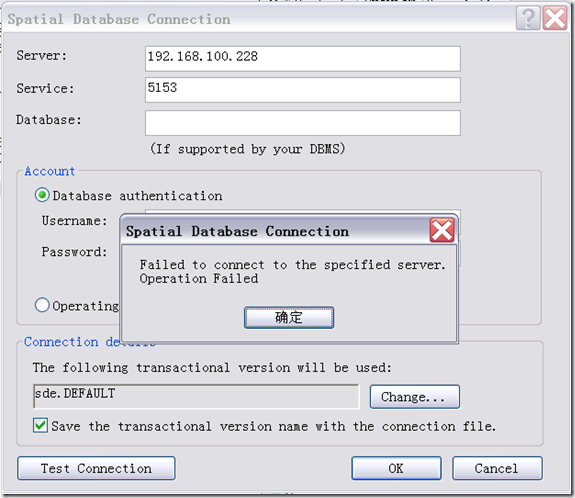
今天在测试环境中,使用ArcCatalog连接到一个SDE服务的时候,报了如下一个错误:
到测试服务器上查看5153的端口的确处于监听状态:
192.168.100.228 [sde ~]$ netstat -lnp|grep giomgr
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
tcp 0 0 0.0.0.0:5151 0.0.0.0:* LISTEN 3739/giomgr
tcp 0 0 :::5153 :::* LISTEN 20002/giomgr
udp 0 0 127.0.0.1:53531 0.0.0.0:* 3739/giomgr
unix 2 [ ACC ] STREAM LISTENING 12022 3739/giomgr /tmp/s.esri_sde.iomgr
unix 2 [ ACC ] STREAM LISTENING 301404 20002/giomgr /tmp/s.esri_sde_db2.iomgr
查看giomgr跟DB2之间的连接,也正常:
192.168.100.228 [sde ~]$ db2 list applications
Auth Id Application Appl. Application Id DB # of
Name Handle Name Agents
-------- -------------- ---------- -------------------------------------------------------------- -------- -----
SDE giomgr 1873 *LOCAL.db2inst1.101231043648 MYDB 1
SDE db2jcc_applica 1853 192.168.100.210.27557.101231043 MYDB 1
SDE giomgr 1872 *LOCAL.db2inst1.101231043647 MYDB 1
这里需要注意的是:
在oracle数据库中,启动服务后只会有一个giomgr进程连接到实例上,但是在DB2,起一次SDE服务会有两个giomgr进程连接到实例上。
思来想去,估计是防火墙有问题,5153端口没有放开:
192.168.100.228 [root ~]$ iptables -L -n
Chain INPUT (policy ACCEPT)
target prot opt source destination
RH-Firewall-1-INPUT all -- 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
RH-Firewall-1-INPUT all -- 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain RH-Firewall-1-INPUT (2 references)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmp type 255
ACCEPT esp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT ah -- 0.0.0.0/0 0.0.0.0/0
ACCEPT udp -- 0.0.0.0/0 224.0.0.251 udp dpt:5353
ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:631
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:631
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
LOG tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:21 LOG flags 0 level 4
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:21
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:1158
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:1521
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:5560
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:60000
LOG tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5151 LOG flags 0 level 4
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5151
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:6500
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
果然5153端口没有放开,
编辑/etc/sysconfig/iptables文件,将5153端口放开:
重启iptable服务后,搞定
192.168.100.228 [root ~]$ vi /etc/sysconfig/iptables
192.168.100.228 [root ~]$ vi /etc/sysconfig/iptables
192.168.100.228 [root ~]$ service iptables restart
清除防火墙规则: [确定]
把 chains 设置为 ACCEPT 策略:filter [确定]
正在卸载 Iiptables 模块: [确定]
应用 iptables 防火墙规则: [确定]
载入额外 iptables 模块:ip_conntrack_netbios_ns ip_conntrac[确定]
192.168.100.228 [root ~]$ iptables -L -n
Chain INPUT (policy ACCEPT)
target prot opt source destination
RH-Firewall-1-INPUT all -- 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
RH-Firewall-1-INPUT all -- 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain RH-Firewall-1-INPUT (2 references)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmp type 255
ACCEPT esp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT ah -- 0.0.0.0/0 0.0.0.0/0
ACCEPT udp -- 0.0.0.0/0 224.0.0.251 udp dpt:5353
ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:631
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:631
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
LOG tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:21 LOG flags 0 level 4
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:21
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:1158
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:1521
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:5560
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:60000
LOG tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5151 LOG flags 0 level 4
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5151
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5153
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:6500
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
文章来源:http://blog.csdn.net/liufeng1980423/article/details/6109394
到测试服务器上查看5153的端口的确处于监听状态:
192.168.100.228 [sde ~]$ netstat -lnp|grep giomgr
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
tcp 0 0 0.0.0.0:5151 0.0.0.0:* LISTEN 3739/giomgr
tcp 0 0 :::5153 :::* LISTEN 20002/giomgr
udp 0 0 127.0.0.1:53531 0.0.0.0:* 3739/giomgr
unix 2 [ ACC ] STREAM LISTENING 12022 3739/giomgr /tmp/s.esri_sde.iomgr
unix 2 [ ACC ] STREAM LISTENING 301404 20002/giomgr /tmp/s.esri_sde_db2.iomgr
查看giomgr跟DB2之间的连接,也正常:
192.168.100.228 [sde ~]$ db2 list applications
Auth Id Application Appl. Application Id DB # of
Name Handle Name Agents
-------- -------------- ---------- -------------------------------------------------------------- -------- -----
SDE giomgr 1873 *LOCAL.db2inst1.101231043648 MYDB 1
SDE db2jcc_applica 1853 192.168.100.210.27557.101231043 MYDB 1
SDE giomgr 1872 *LOCAL.db2inst1.101231043647 MYDB 1
这里需要注意的是:
在oracle数据库中,启动服务后只会有一个giomgr进程连接到实例上,但是在DB2,起一次SDE服务会有两个giomgr进程连接到实例上。
思来想去,估计是防火墙有问题,5153端口没有放开:
192.168.100.228 [root ~]$ iptables -L -n
Chain INPUT (policy ACCEPT)
target prot opt source destination
RH-Firewall-1-INPUT all -- 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
RH-Firewall-1-INPUT all -- 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain RH-Firewall-1-INPUT (2 references)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmp type 255
ACCEPT esp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT ah -- 0.0.0.0/0 0.0.0.0/0
ACCEPT udp -- 0.0.0.0/0 224.0.0.251 udp dpt:5353
ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:631
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:631
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
LOG tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:21 LOG flags 0 level 4
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:21
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:1158
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:1521
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:5560
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:60000
LOG tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5151 LOG flags 0 level 4
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5151
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:6500
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
果然5153端口没有放开,
编辑/etc/sysconfig/iptables文件,将5153端口放开:
重启iptable服务后,搞定
192.168.100.228 [root ~]$ vi /etc/sysconfig/iptables
192.168.100.228 [root ~]$ vi /etc/sysconfig/iptables
192.168.100.228 [root ~]$ service iptables restart
清除防火墙规则: [确定]
把 chains 设置为 ACCEPT 策略:filter [确定]
正在卸载 Iiptables 模块: [确定]
应用 iptables 防火墙规则: [确定]
载入额外 iptables 模块:ip_conntrack_netbios_ns ip_conntrac[确定]
192.168.100.228 [root ~]$ iptables -L -n
Chain INPUT (policy ACCEPT)
target prot opt source destination
RH-Firewall-1-INPUT all -- 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
RH-Firewall-1-INPUT all -- 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain RH-Firewall-1-INPUT (2 references)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmp type 255
ACCEPT esp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT ah -- 0.0.0.0/0 0.0.0.0/0
ACCEPT udp -- 0.0.0.0/0 224.0.0.251 udp dpt:5353
ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:631
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:631
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
LOG tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:21 LOG flags 0 level 4
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:21
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:1158
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:1521
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:5560
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:60000
LOG tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5151 LOG flags 0 level 4
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5151
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:5153
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:6500
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
文章来源:http://blog.csdn.net/liufeng1980423/article/details/6109394